by Guillermo J. Rosas, Faculty, Information Technology, Metropolitan Community College
General Disclaimer
This write-up has been provided for informational and educational purposes only.I strongly discourage students and staff from attempting the same exploration.
The exploratory tasks discussed in this write-up were performed on a virtual machine hosted on a physical machine separated from other computers on my home network. The host machine is scheduled to be rebuilt during quarter break and it is not used aside from experimenting. It’s important to note, the destination website could have potentially hosted malware and my machine could have become infected in the process of this write-up.
In other words, enjoy the write-up but don’t try this at home, kids.
Introduction
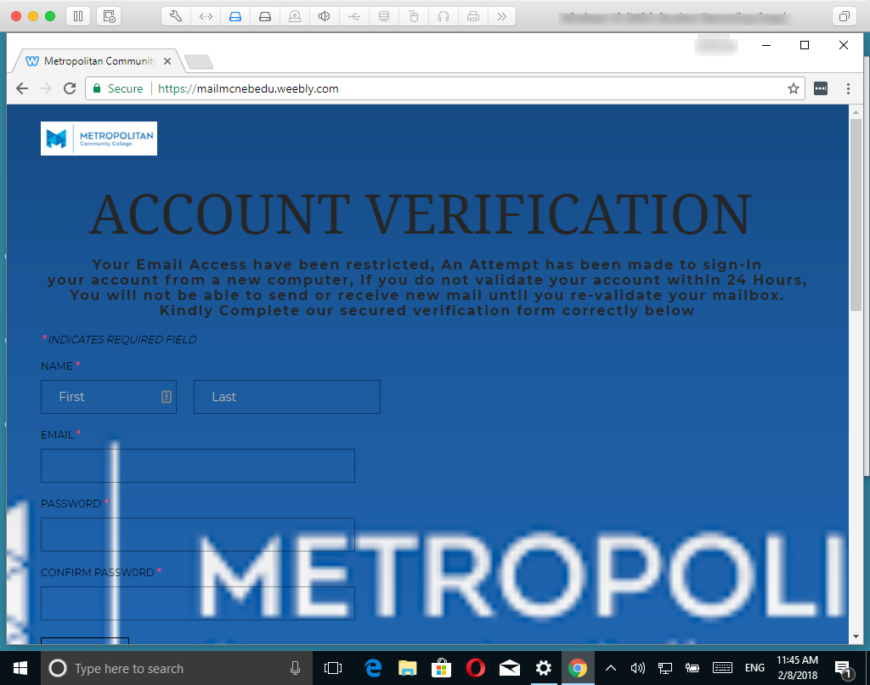
Many of us have been the recipients of a large number of phishing emails over the past few weeks. Figure 1 (below) shows one of the many emails I received earlier this week.
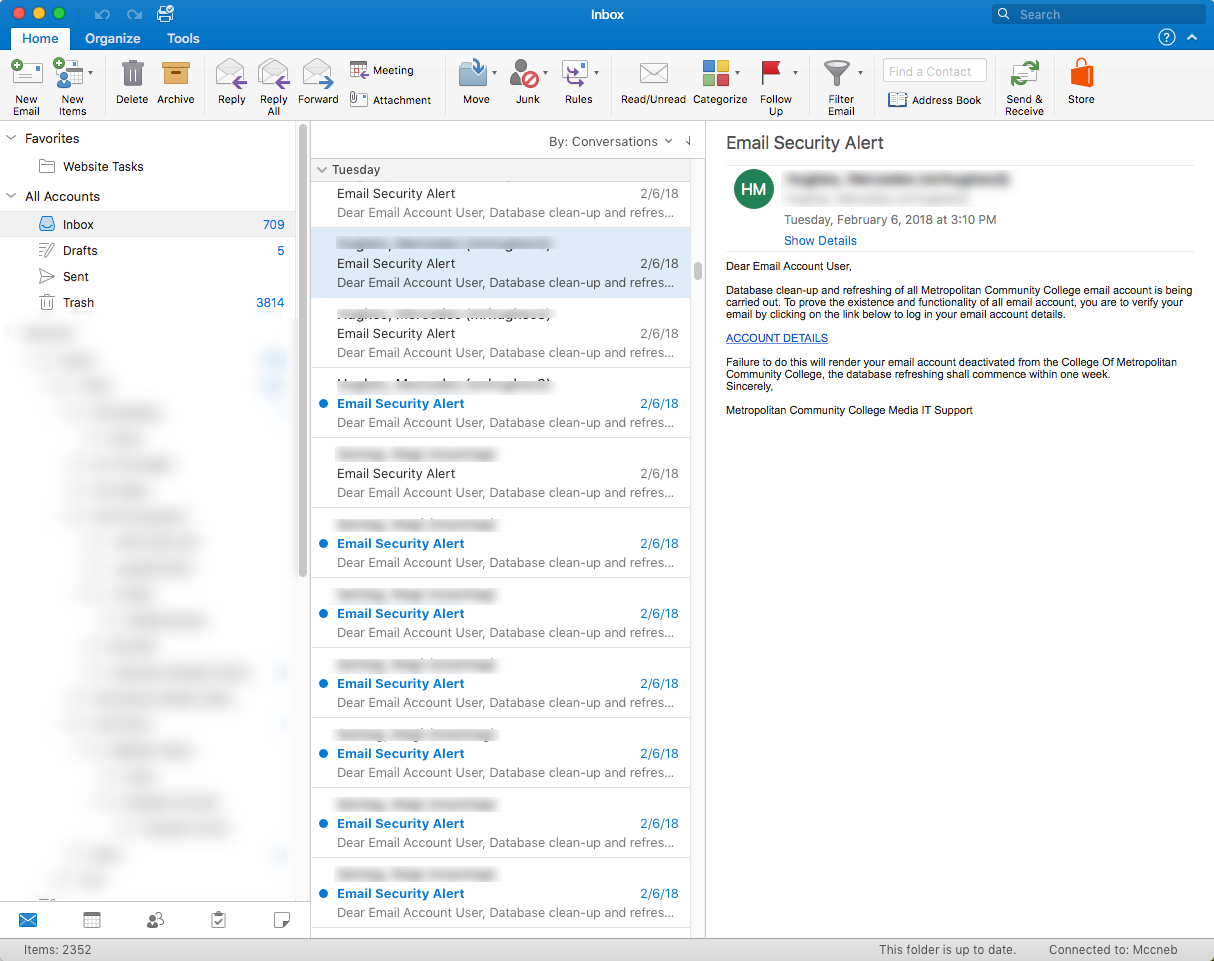
As shown in Figure 1, the email directs the recipient to verify their email by clicking on a link provided in the body of the email.
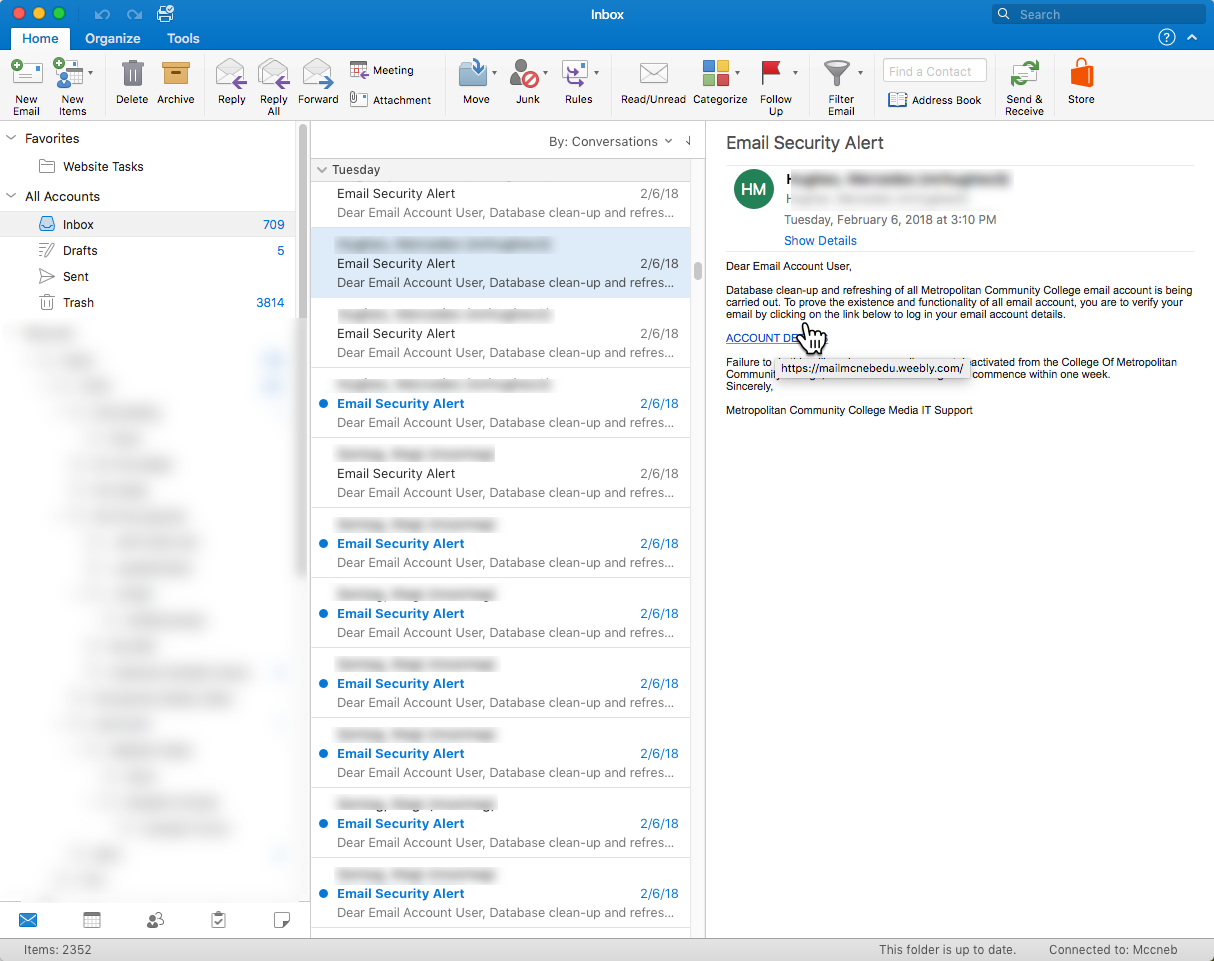
If you hover over the link (without clicking on it), Outlook will display the destination URL (or where the link will take you if you click on it), which is mailmcnebedu.weebly.com (Figure 2). This should be a huge red flag — Weebly is a web-hosting service that provides a simple drag-and-drop interface building to help small organizations quickly and easily build websites. The important thing is, this URL is pointing to a site that is not MCCNEB.EDU.
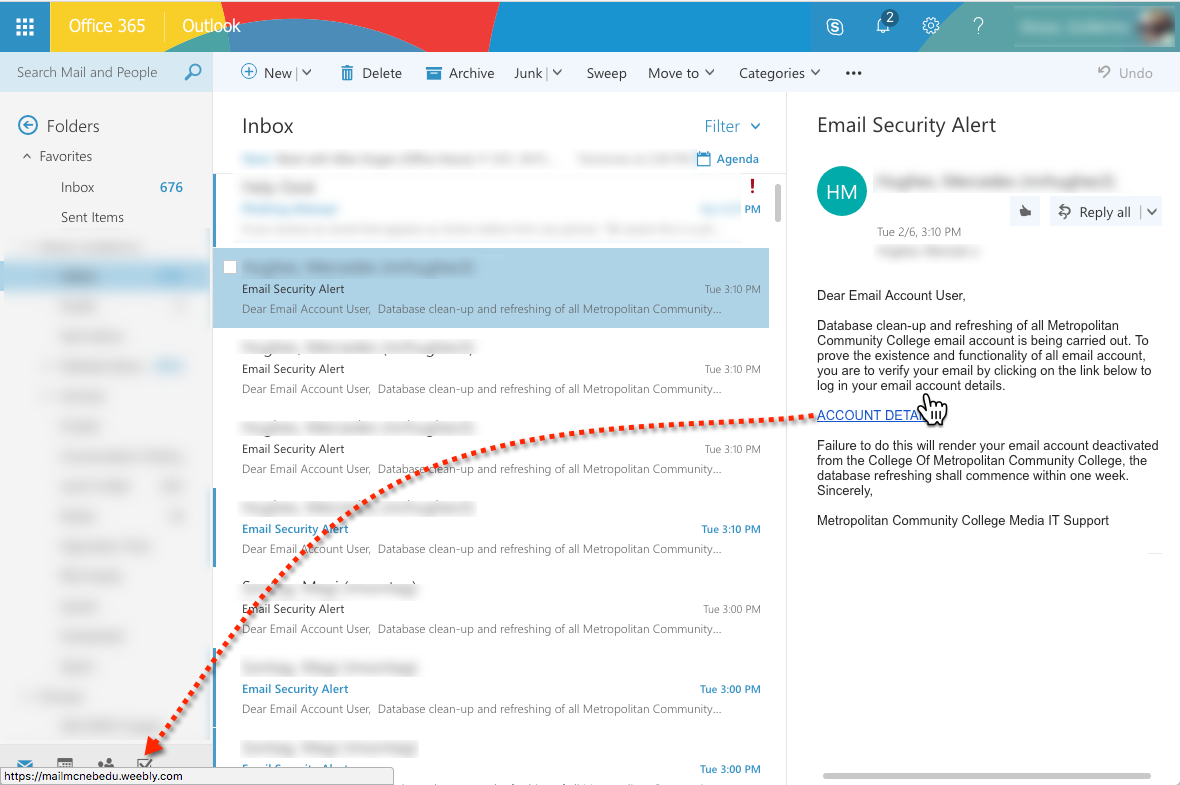
The browser-based version of Outlook (and other email services such as GMail) will also display a link’s destination URL when hovered over; however, the destination URL will appear at the bottom of the browser window – as shown in Figure 3.
Consider for a moment, the websites you browse to access school resources:
- www.mccneb.edu will take you to the school’s webpage
- https://myway.mccneb.edu/ will take you to MyWay, where you can access your student email, OneDrive, Blackboard, etc.
- https://blackboard.mccneb.edu/ will take you to the Blackboard home page.
The one common thread amongst the websites listed above, is that they all end with mccneb.edu — in no instance does a school website end with .com or with weebly.com
So, What Happens If I Click On The Link?
I thought you’d never ask . . .
I suspect a number of students have clicked on the links in the phishing emails. My suspicion stems from the fact that the emails are coming from internal addresses.
Out of curiosity, let’s see what happens when we browse to one of the links in a phishing email….
Browsing to mailmcnebedu.webly.com took me to the page shown in Figure 4 (below). What a nice page.
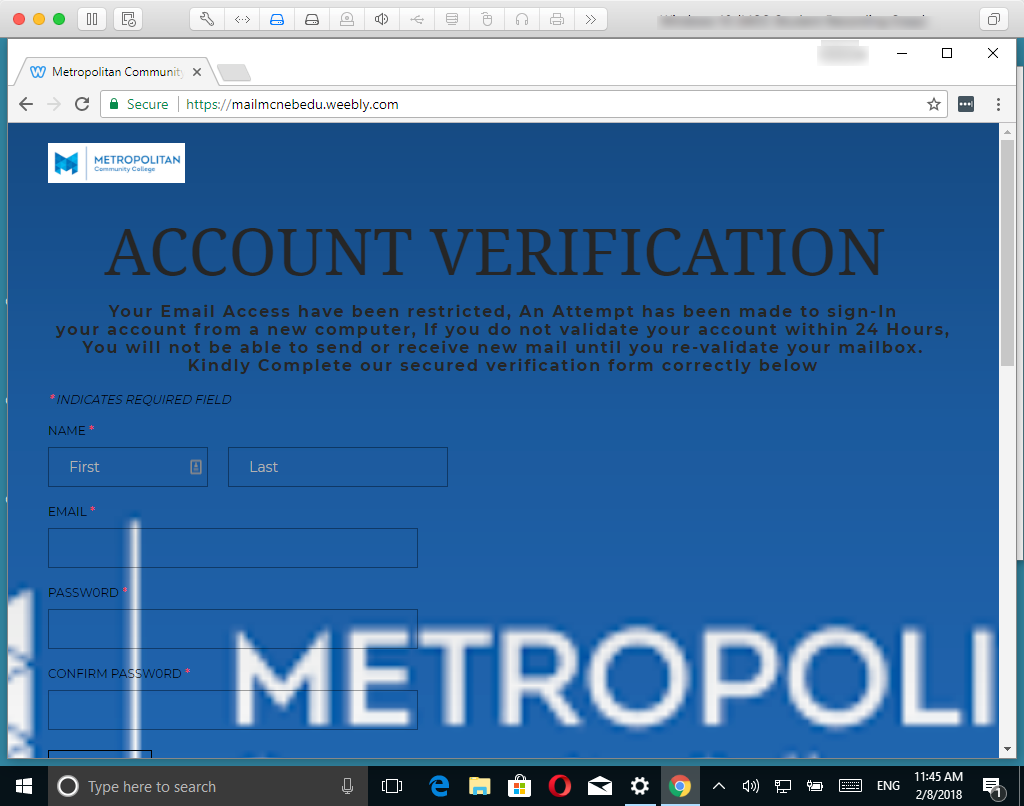
Note the information being collected by the form shown in Figure 3: First and Last Name, Email Address and Password.
The page does contain Metropolitan Community College branding – note the use of the school’s logo.
Let’s scroll down to the bottom of the page (Figure 5).

A big red flag, in my mind (aside from the abhorrent look of the page and the fact that the page is hosted on weebly.com) are:
- the giant Create a free website button; and,
- the Powered by Weebly graphic
Let’s take a quick look at the source code of the webpage (Figure 6).
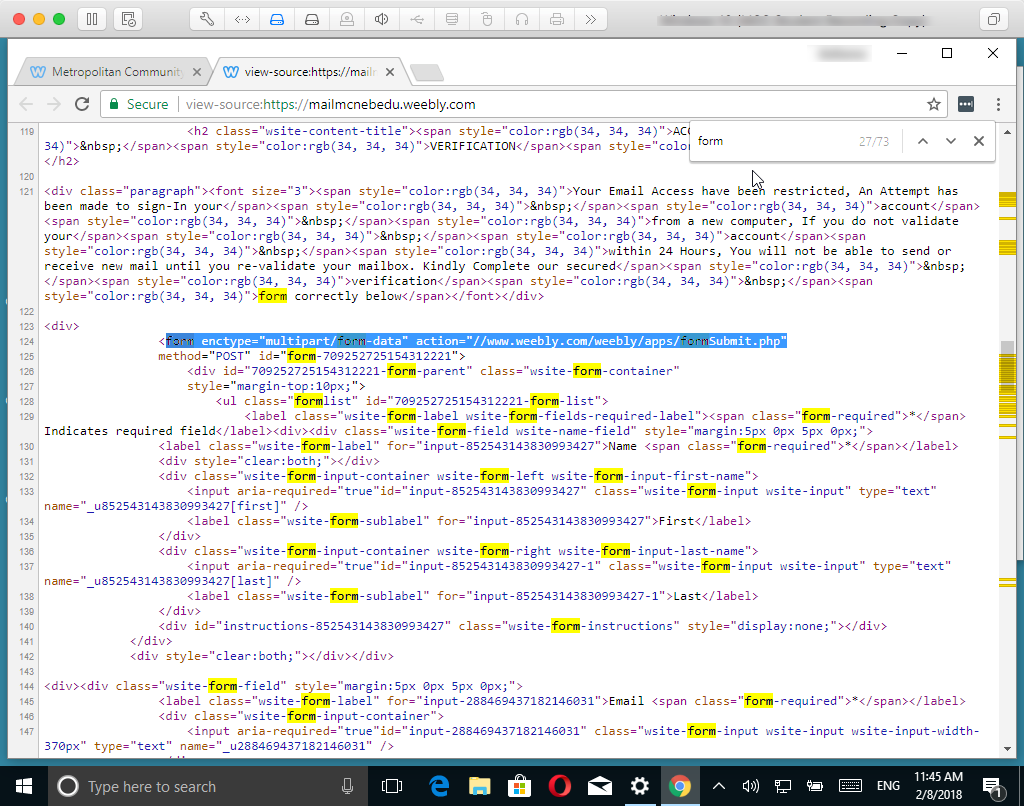
In Figure 6 (above), I’ve highlighted the HTML that defines the initial part of the form shown in Figure 4.
Without getting too technical, when a visitor fills out the form and clicks Submit, the information contained in the form will be sent to www.weebly.com/weebly/apps/formSubmit.php — basically, when the user clicks Submit, the information in the form will be sent to a script on the server. I do not have insight into that script but I suspect the script simply collects the information and writes it into a database, collecting usernames and passwords from users who clicked on the link in the phishing email and subsequently provided their credentials.
Now this guy has someone’s credentials.

So What?
So, a hacker has my MCC credentials — so what!?
Consider what you have access to at the school. Even if you’re a student, you have access to:
- Your email account;
- Your classes via Blackboard;
- Your academic record;
- Your financial information;
- Your demographic information including home address, telephone number, etc.; and,
- Your contacts
And so forth and so on. The key thing in that list is your information. At MCC, nobody should have access to your information but you, some staff, and your instructors.
How Do I Stay Safe?
Healthy skepticism.
- Be wary of any links contained in email even if the email comes from a known or trusted contact. Consider, the phishing attacks of late are coming from MCC user accounts.
- Preview links contained in emails by hovering over them in Outlook to display the destination URL (where the link will take you if you click on it).
- MCC will never ask you to provide your username or password
- Change your password frequently. The school will make you change your password every 90 days, but why wait?
Help! I Clicked A Link!
If you happen to click on a suspicious link and if you think your credentials may be compromised, change your password by visiting the MCC password station at https://www.mccneb.edu/Current-Students/Student-Tools/Password-Station.aspx

Guillermo J. Rosas is a full-time faculty member in the Business and Information Technology Department at Metropolitan Community College (MCC). He has over 18 years of experience in the field of Information Technology. Prior to joining MCC’s faculty, Guillermo worked as a Network Defense technician at the USSTRATCOM Network Operations Center.
Guillermo holds a BS in Information Systems from Bellevue University, and a MBA from Bellevue University. His professional certifications include: A+, Security+, Network+, Linux+, Certified Ethical Hacker, and Certified Information System Security Professional (CISSP).